30 DAYS VIP
Free PREMIUM UDP CUSTOM and UDP REQUST
How to Use this UDP server
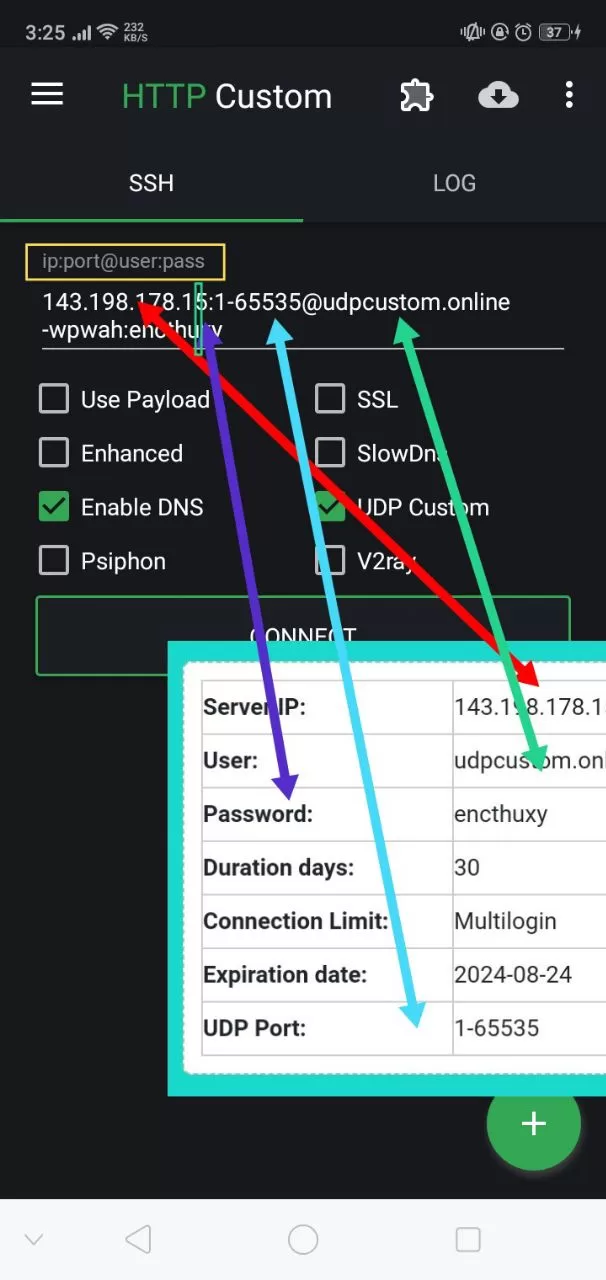
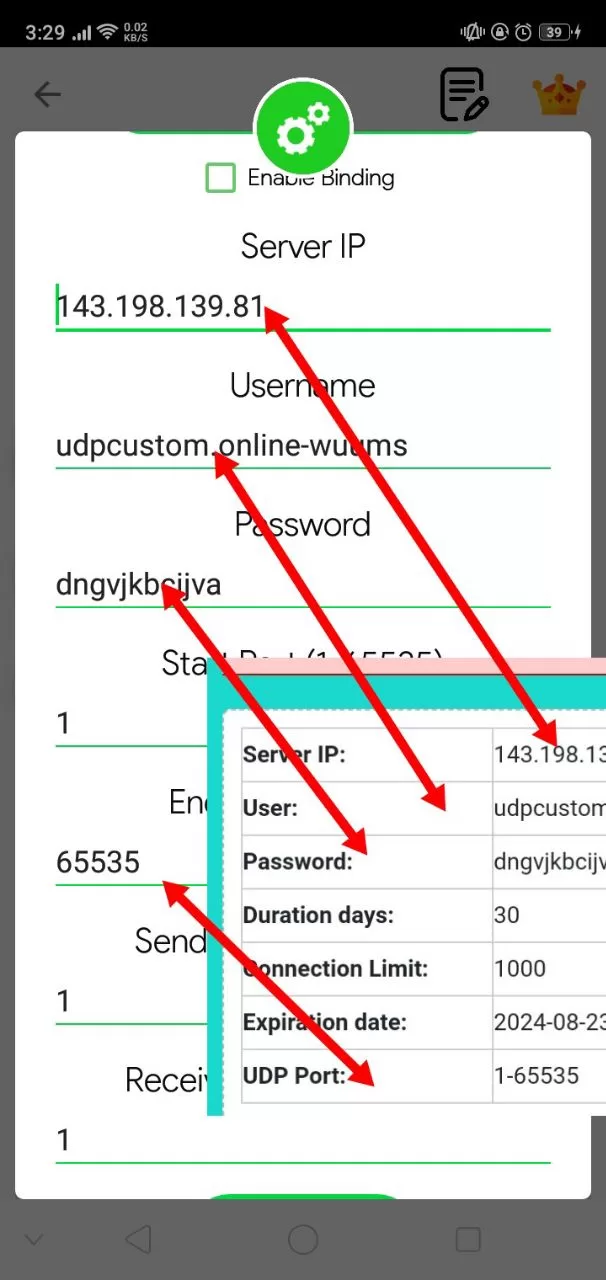
How to Use HTTP Custom
How to Use Socks IP
Ensuring Data Security with SSH and VPN Technologies
In today’s digital age, maintaining the confidentiality, integrity, and authenticity of data transmitted over public networks is crucial. Technologies like SSH (Secure Shell) and VPN (Virtual Private Network) play a vital role in achieving this by encrypting all data passing through them. This article delves into how these technologies safeguard data and ensure secure communication over the internet.
Confidentiality: Keeping Data Private
One of the primary benefits of SSH and VPN technologies is their ability to maintain data confidentiality. By utilizing encryption, these technologies ensure that any data transmitted over the network is unreadable to unauthorized parties. When data is encrypted, it is transformed into a coded format that can only be deciphered by someone who has the correct decryption key.
Even if an attacker manages to intercept the data as it travels over the internet, the encryption renders the data useless without the decryption key. This high level of security makes SSH and VPN ideal for protecting sensitive information from prying eyes, ensuring that data remains confidential.
Data Integrity: Ensuring Data Accuracy and Consistency
Data integrity is another critical aspect of secure communications. As data travels through the vast expanse of the internet, it passes through numerous servers and countries, exposing it to potential threats like loss, damage, or tampering.
SSH and VPN technologies help maintain the integrity of data by employing various mechanisms to detect and prevent any alterations during transmission. For instance, they use cryptographic hash functions to generate unique signatures for data packets. If any modification occurs, the mismatch in signatures alerts the system, ensuring that the data remains unaltered from the point of transmission to its destination.
Source Authentication: Verifying Data Origins
Authentication is the process of verifying the identity of the data source. SSH and VPN technologies incorporate robust authentication mechanisms to ensure that the data received comes from a legitimate and verified source. This is done through several methods, such as digital certificates, public key infrastructure (PKI), and pre-shared keys.
When data is sent over SSH or VPN, the technology checks the credentials of the sending party. Only when the source is authenticated, the data is allowed to proceed. This process prevents unauthorized entities from sending data and guarantees that the information comes from a trusted source, thus preventing data spoofing and other malicious activities.
Conclusion
SSH and VPN technologies are indispensable tools in the modern era of digital communication. By providing encryption to ensure confidentiality, mechanisms to maintain data integrity, and robust authentication processes, they safeguard data against a multitude of threats. Implementing these technologies is essential for anyone looking to protect sensitive information and maintain secure communications over public networks. As cyber threats continue to evolve, the use of SSH and VPN will remain a cornerstone of effective cybersecurity strategies.
